COUNTERMEASURES AGAINST HOLOGRAM COUNTERFEITING
New Light Industries, Ltd.
Presented at the International Symposium and Product Presentation for Optical Information Storage and Display (Zurich, Switzerland), October 14-16, 1987.
Abstract
A number of ways to counterfeit holograms are described, along with proposed counter-measures. Probable effectiveness of the countermeasures is discussed.
Introduction
It is fashionable to think of holograms as being virtually uncounterfeitable. The fact of the matter is that holograms in the form currently used in security are almost trivially easy to counterfeit. Although we know of no instances of counterfeited holograms in the security business per se, there are undeniable cases where commercial hologram designs have been counterfeited.
The purpose of this presentation is to explore the more straightforward methods by which holograms can be counterfeited, and to offer ways that hologram counterfeiting may be prevented.
1. Types of Holograms
There are two types of holograms currently produced in substantial quantities.
Embossed holograms are the type used in most security applications, such as credit cards and passports. Embossed holograms are easily mass produced at a low cost. They are very thin when used in the form of hot stamping foil, but are highly durable. An embossed hologram is a microscopically detailed surface relief pattern analobous to a phonograph record or a compact disk.
Denisyuk holograms are another type of hologram that has been considered for security applications but has not yet received wide use. Each Denisyuk hologram must be made with a laser in a high-resolution holographic recording medium, so this type of hologram is unavoidably more expensive and slower to produce. Also, Denisyuk holograms are relatively thick in their present form and are rather easily damaged
2. Counterfeiting Methods
Embossed Holograms:
From the point of view of a counterfeiter, embossed holograms are potentially the path to easy money. There are four straightforward ways to counterfeit embossed holograms, and we can be sure that these ways will be learned by counterfeiters.
- holographic copying in one step
- holographic copying in two steps
- mechanical copying
- re-origination
These methods will be examined in greater detail later. Each method is relatively simple and can be used to produce a passable copy of any embossed hologram that exists today.
Denisyuk Holograms:
Denisyuk holograms are more difficult to counterfeit in some ways than embossed holograms. First of all, Denisyuk holograms cannot be mechanically replicated or counterfeited because their effect depends upon a complex three dimensional structure that extends through the thickness of the recording material. Denisyuk holograms can only be copied by optical methods. These methods are:
- holographic copying in one step (contact printing)
- holographic copying in two steps
- re-origination
Again, it is relatively simple to make a passable counterfeit of a Denisyuk hologram by these methods.
3. Countermeasures
The counterfeiting methods exploit certain properties that
today's holograms have. If holograms for security purposes are
made differently, counterfeiting by those methods can be
effectively prevented.
Briefly, these methods are:
- * use materials in hologram copies which make the laser an ineffective tool for the counterfeiter.
- * covertly store machine-readable information in the holograms to make re-origination ineffective.
- * use materials and structures in and with holograms to make mechanical copying ineffective.
- * use imagery which cannot easily be re-originated.
- * include variable information in holograms.
- * alter the processing of the hologram to introduce distortions which are difficult to copy.
�
I. PRESENT MANUFACTURING AND USE OF HOLOGRAMS IN SECURITY
A. Embossed holograms are made by the process illustrated in Figure 1, Figures 2a, 2b, 2c, and Figure 3. The embossing is normally done into either a plastic film such as PVC or polyester and used for adhesive labels, or into a hot stamping foil base. These two options are illustrated in Figures 4 and 5. The holograms are then applied to a document or product, and the presence of the hologram is intended to be a reliable indication that the document or product is valid.
B. Denisyuk holograms are made by the process illustrated in Figure 6 (forming a Denisyuk hologram). Duplicates are made by repeating the process. Denisyuk holograms are recorded into silver halide film, photopolymer film, or dichromated gelatin film. The resulting hologram is finally laminated into a card or applied to a product as a tag or label.
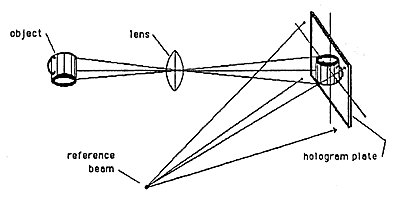
Figure 1: Forming a Hologram
�
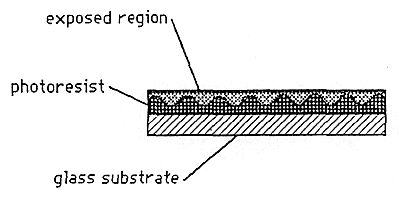
Figure 2a: Exposed Photoresist Plate
�
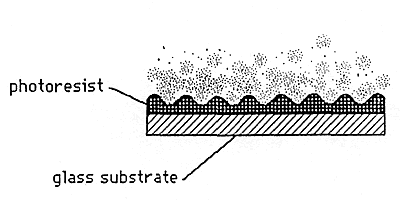
Figure 2b: Development of Photoresist
�
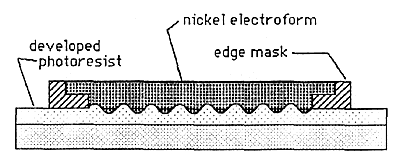
Figure 2c: Nickel Electroforming
�
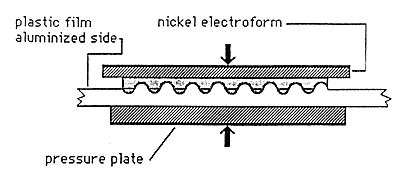
Figure 3: Embossing a Hologram
�
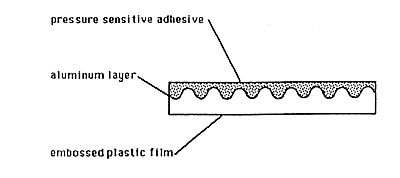
Figure 4: Adhesive Labels
�
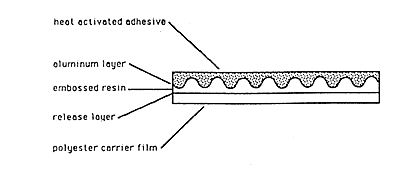
Figure 5: Hot Stamping Foil
�
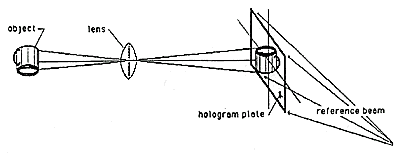
Figure 6: Forming a Denisyuk Hologram
�
II. COUNTERFEITING METHODS & COUNTERMEASURES
�
A. Counterfeiting Methods
Today's holograms are rather easily counterfeited by the following processes:
1. Re-origination is the time-honored method of counterfeiting. It involves creating a faithful imitation of the original artwork, using a valid copy as a guide. The Visa hologram, for example would be very straightforward to copy by re-origination. The image is there on every card for a skilled sculptor to recreate as a solid model. Once a good model is made, it is easy for any skilled holographer to make holograms and copies that will pass even a careful inspection. Visa, seeking a second source for their holograms, gave Light Impressions the original Visa model after it had been broken. We repaired it and made holograms that American Banknote has described as indistinguishable from their own holograms made from the unbroken model.
"Kinegrams", the type of holograms made by Landis & Gyr, are significantly more difficult to re-originate because they are not made from a model. They are instead a type of "stereogram", made from a sequence of two dimensional images. A sophisticated counterfeiter, however, would be able to re-originate a kinegram. These holograms, being embossed holograms, are subject to the same counterfeiting methods as other embossed holograms.
2. One-step copying is accomplished by simply contact copying the hologram. In one approach (Fig. 7), a holographic film is placed against the security hologram and illuminated with a laser. For a Denisyuk hologram, the film is merely developed and used directly. For an embossed hologram, the film is developed, and metallized, and the result is a passable imitation of the original hologram. In another approach, a photoresist coated film is placed against the hologram and illuminated with a laser. The photoresist is developed and electroplated. The electroform is then used to emboss counterfeit copies of the hologram.
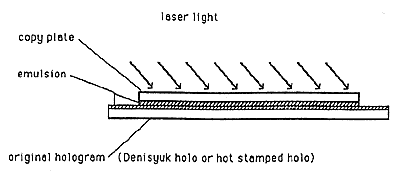
Figure 7: One-Step (contact) Copying
3. Two-step copying is accomplished by illuminating the original hologram with a laser and recording the diffracted light in a second hologram (Figures 8a & 8b). Next, the second hologram is illuminated to produce a replica of the image in the original hologram, and the image is used to make a duplicate of the original hologram. For a Denisyuk hologram, the duplicate is the counterfeit. For an embossed hologram, the final hologram is recorded in photoresist so that it can be electroplated and used to emboss counterfeit copies of the hologram. This process is only slightly more complicated than contact copying, and produces excellent copies.
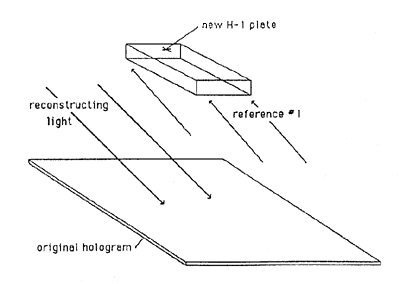
Figure 8a: Step 1 of Two-Step Copying
�
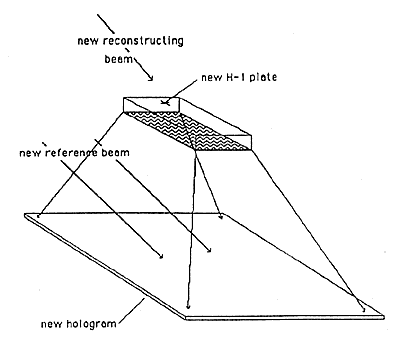
Figure 8b: Step 2 of Two-Step Copying
4. Mechanical copying is accomplished by uncovering the embossed surface of the hologram and using it as a form to produce an electroplated copy. The electroplated copy can then be used to emboss counterfeit copies of the original hologram. If the counterfeiter can obtain unused original holograms, the process is trivially easy. If he only has a Visa card to work from, the process is a bit more messy. Figure 9 illustrates one way to work from a credit card.
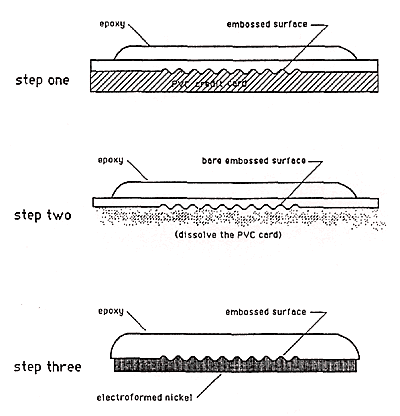
Figure 9: Mechanical Copying
�
B. Countermeasures
1. Complex Imagery or Hidden Information
Re-origination can be prevented only by including hidden information or by making the image so complicated that it is not worth the counterfeiter's time to duplicate it. Hidden information is of value only if the counterfeiter cannot find it or duplicate it. Hidden information is of only limited value unless it is detectable at the point of use of the security document or credit card. So, effective use of hidden information requires some sort of relatively simple and inexpensive reading device or decoding device.
Several ways are known for encoding holograms to make them readable only with a suitable decoding device. One such method (fiber optic coding/decoding) is shown in Figures 10a, 10b, and 10c. Other methods (phase plate encoder/decoder and off-surface recording) are shown in Figures lla, llb and 12.
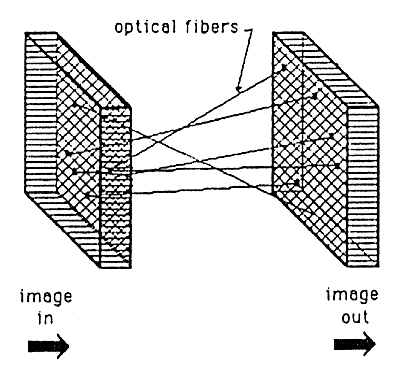
Figure 10a: Fiber-Optic Encoder/Decoder
�
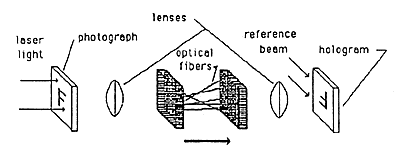
Figure 10b: Encoding
�
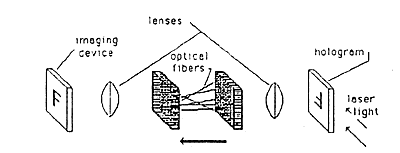
Figure 10c: Decoding
�
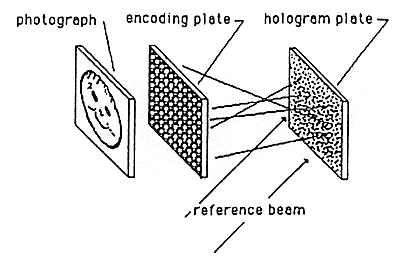
Figure 11a: Diffuser Encoding
�
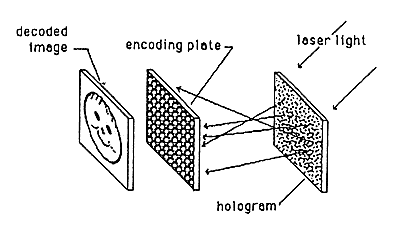
Figure 11a: Diffuser Decoding
�
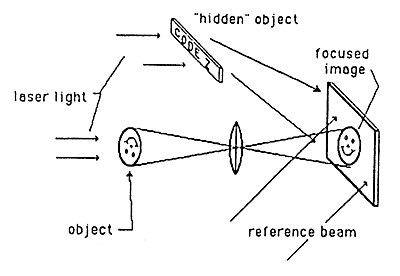
Figure 12: Hidden Image
Complicated imagery can be produced by the stereogram process; the kinegrams of Landis & Gyr are an example. Stereograms are usually made by one of the processes illustrated in Figures 13, 14, and 15. These stereogram processes all involve making a complex image as a combination of simple two-dimensional images.
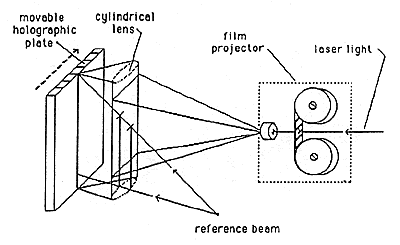
Figure 13: Lenticular Stereogram System
�
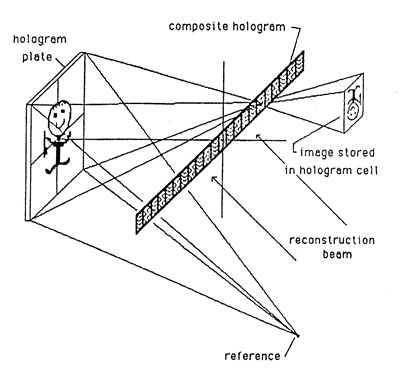
Figure 14: Two-Step Stereogram
�
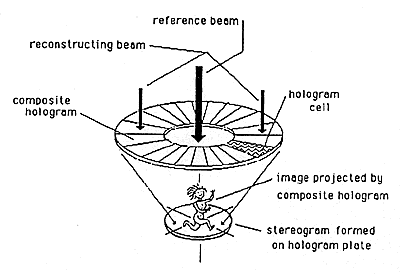
Figure 15: Disk Hologram
None of the methods shown in Figures 10 through 15 can prevent direct copying, simply because even the most complex imagery, even if hidden or encoded, is faithfully copied by one-step, two-step, or mechanical methods.
Limitations:
Without a reader, complex imagery only works if it is simple enough that an untrained observer can detect an imperfect copy. We are not convinced that the requirements of complexity and simplicity leave anything in between.
Many systems that require a decoding device can be beaten by a counterfeiter who steals the device, because the method of encoding is usually implied by the method of decoding.
�
2. Variable Processing Parameters
A way has been proposed by Jeff Blythe to produce a Denisyuk hologram which would be extremely difficult to copy using either one-step or two-step copying. Blythe's proposal is to randomly vary the exposure, development time, or other processing parameters to produce variable shrinkage across the hologram. The result is a hologram whose color varies from point to point. A variation of Blythe's method has been demonstrated by Applied Holographics, resulting in a hologram whose color or brightness varies according to a predetermined pattern.
Because a laser is monochromatic, the brightness of a simple optical copy of a variable-shrinkage hologram varies dramatically with the shrinkage of the film. In fact, if the film is thick enough or the shrinkage is extreme enough, the copy will have no image at all in most of its regions.
A variable-thickness Denisyuk hologram is illustrated in Figure 16.
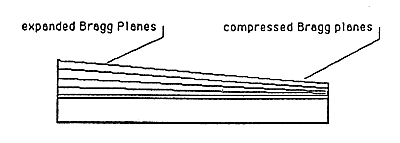
Figure 16: Variable-Thickness Denisyuk Hologram Figure
Limitations:
It is probably possible to copy a variable-thickness Denisyuk hologram by using a tunable dye laser to record a series of copies in different wavelengths, but it would be a difficult task even for a highly skilled holographer. However, the greatest counterfeiting risk for this type of hologram would be the ease of re-originating the hologram. Thickness variations, unless controlled carefully in ways that are difficult to simulate and easy to recognize, could be produced easily.
�
3. Variable Information
Holograms are riskier to counterfeit if they include variable information such as serial numbers, dates, or encoded personal information. A liquid crystal display may be used as shown in Figure 17 to record variable information in a Denisyuk hologram. Because each Denisyuk hologram is separately recorded, this type of variable information is completely practical.
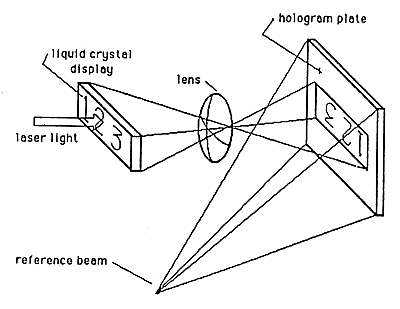
Figure 17: Hologram with Variable Information
Because embossed holograms are mechanically reproduced, it is not practical to holographically record variable information in them. However, it is possible to record variable information in the process of applying holographic hot stamping foil to a substrate as shown in figure 18. It is also possible to demetallize an embossed hologram selectively as illustrated in Figure 19 and therefore perform a sort of "reverse printing" operation for providing variable information.
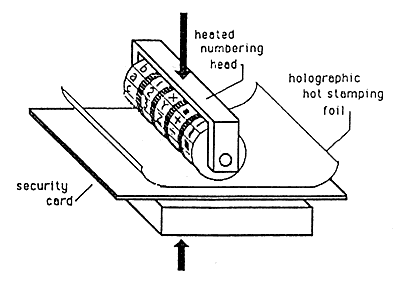
Figure 18: Variable Information by Hot Stamping
�
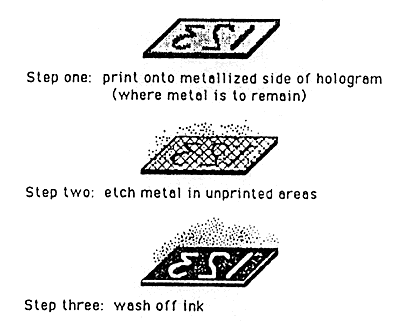
Figure 19: Selective Demetallization for Variable Information
Limitations:
It would not be very difficult for a counterfeiter to use these simple variable information techniques, if the variable, information is in the form of ordinary numbers, bar codes, or words. In order for these techniques to be effective, the variable information must be recorded in a form that is not easily reproduced. We consider a variation on this approach, which will be discussed later, to be highly promising as a high-security feature in future holographic security systems.
�
4. Special Materials
Optical methods of copying holograms depend upon the ability of a single laser beam to reconstruct and record the image from a valid hologram. The use of variable processing parameters to produce variable-thickness Denisyuk holograms as described above is one way to greatly complicate the copying process.
Another class of methods for complicating the optical copying process is to make the hologram of materials which alter the polarization of light or selectively filter out or scatter particular wavelengths of light. Alternatively, the hologram can be overcoated or laminated under such materials. Figure 20 represents a copy made of a hologram overcoated with a birefringent material.
Fig. 20: A Hologram Copied Through a Birefringent Filter
Limitations:
The use of special materials can complicate the optical copying process, but cannot make optical copying impossible. The combination of tunable dye lasers and polarization rotating optics in the hands of a dedicated and highly skilled holographer is enough to permit counterfeiting.
�
5. Multiply-Connected Holograms
Mechanical copying is the simplest method for counterfeiting. Denisyuk holograms cannot be copied mechanically, but embossed holograms as they are made today can be mechanically copied rather easily by the method shown in Figure 9. There may conceivably be special formulations of the plastics for hologram embossing or for making credit cards, which will prevent the use of ordinary organic solvents for removing the substrate and leaving the embossed hologram surface intact.
However, we believe that the most effective approach to preventing mechanical copying of embossed holograms is to make the holograms multiply-connected. Multiple connectivity means that the hologram is composed of dots or else is punched full of holes. A multiply-connected hologram is illustrated in Figure 21.
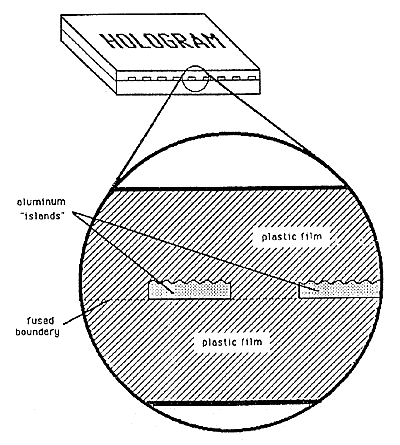
Figure 21: "Multiply Connected" Hologram
Multiple connectivity makes the use of solvents or other means to uncover the embossed surface of a hologram as in Figure 9 very difficult. In the hologram of Figure 21, it is apparent that an attempt to dissolve one side of the hologram away to uncover the aluminum surface would very likely result in obliterating parts of the hologram by undercutting its dots, even if the aluminum were an effective barrier to the solvent. Any unevenness or patterning in the thickness of the coating would compound the complications.
Limitations:
We feel that multiply connected holograms would be virtually immune to mechanical copying, but would not be intrinsically immune to any of the other counterfeiting techniques. Optical copying by one-step or two-step techniques would work just as well on a multiply-connected hologram as any other hologram, but then to make a multiply-connected hologram from the copy would be a complicated task.
�
C. Combined Countermeasures
None of the countermeasures described above, taken alone, is immune to all of the counterfeiting methods. Certain countermeasures in combination, however, promise to be highly effective against all of the counterfeiting methods we have foreseen.
�
1. For Denisyuk Holograms
Denisyuk holograms having patterned variable thickness and containing encoded and hidden variable information will be immune to mechanical copying and difficult to copy optically. If the variable information is hidden or encoded and machine-readable, invalid or re-originated counterfeit holograms will be detected at the point of use by a decoding and validation system.
Advantages/Disadvantages:
Denisyuk holograms tend to be relatively thick, and are not hot-stampable. They must be protected from humidity by overcoating or laminating. They are relatively expensive, compared to embossed holograms.
On the other hand, a Denisyuk hologram can (in principle) be originated in a few minutes at low cost by a relatively uncomplicated system.
�
2. For Embossed Holograms
Embossed holograms combining the features of multiple connectivity and machine-readable encoded variable information, overcoated with a polarization-varying material, will be extremely difficult to copy mechanically or optically. Re-originated counterfeits or invalid holograms will be detectable at the point of use by a decoding and validation system.
The "Ideal Security Hologram"
EMBOSSED
DENISYUK
|
Advantages/Disadvantages:
A disadvantage of embossed holograms is that the production of an embossing master is a time-consuming and relatively expensive process. For small-volume applications, embossed holograms have no apparent security advantages over Denisyuk holograms.
For large-volume applications such as credit cards and telephone cards, embossed holograms have a decisive cost advantage. Embossed holograms may be applied by hot stamping, and they are thin enough to be suitable for use on thin, flexible items such as paper currency and travelers' checks. The greatest advantage of embossed holograms in some applications may be the fact that they are more durable than Denisyuk holograms.
SUMMARY AND PREDICTIONS
There are several methods for counterfeiting today's security holograms. Though we have no indication that those methods have been used yet by counterfeiters in the security field, the proliferation of holographic technology and the high level of activity in the field will surely lead to hologram counterfeiting. In the commercial sector, hologram counterfeiting and copying have been occurring for years.
Straightforward methods exist for preventing the counterfeiting of holograms by these methods. In particular, holograms made with machine-readable variable information, either as variable-thickness Denisyuk holograms or as multiply-connected embossed holograms, should be able to provide a level of security well above that of today's optical security devices, and should provide protection against sophisticated counterfeiters for many years.